At this moment there are 10+ completely new tools hidden in NirSoft Web site. There is no any link to these new tools in NirSoft or in any other Web site.
In order to find these new tools, you need to have some programming knowledge, understanding of Web technology, and other skills.
If you don’t have the ability to find the new tools, you don’t have to worry. All new tools will be published officially in Nirsoft Web site on 01/04/2018 (and this is not a joke of April Fools’ Day, the new tools are real)
First Stage – Finding the first tool.
Here’s the instructions for finding the first new tool hidden in NirSoft Web site:
In the .exe file of the following tools there is an hidden message:
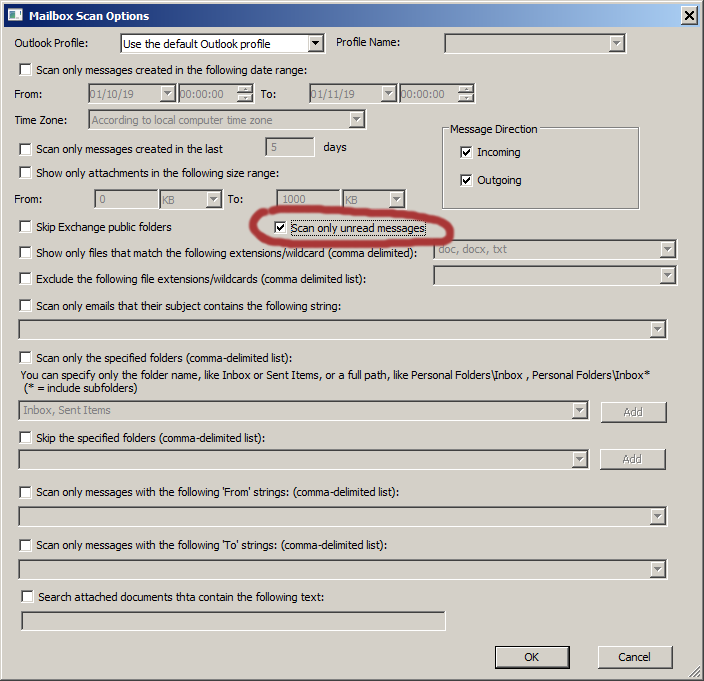
USBDeview, NetworkUsageView, FileTypesMan, LastActivityView, WifiHistoryView, ControlMyMonitor, CSVFileView, TimeZonesView, UninstallView, DevManView, TaskSchedulerView, SoundVolumeView
You can download a zip file with .exe files of all these tools from here.
In order to decrypt the message, you have to XOR all bytes of every .exe file with 0x7f (127) and then search for a short message in English.
It’s recommended to start the search from the end of the file and then move backwards, because the message is stored in the second half of the file.
Also, when there are 32-bit and 64-bit versions of the same tool, it’s recommended to use the 32-bit executable file.
In all tools except of one, the message is a short quote that somewhat represents my own personal worldview.
Only in one tool you’ll find the real thing you’re looking for – a link to a Web page that contains a new tool !
Be aware that the hidden message only contains the html page of the URL, but you can easily find the actual URL because like all NirSoft tools – it’s located
under https://www.nirsoft.net/utils
Second Stage – Finding all other tools
Inside the Web page of the first tool, there is a clue that can lead you to the next tool.
In order to find it, you need some understanding of Web technology (I mean – you have to look inside the HTML of this Web page).
If you find the second tool, then like in the first tool, the Web page of the second tool contains a clue that can lead you to the next new tool. Like in the first tool, the other clues contain only the html page, so you have to add the html page string to https://www.nirsoft.net/utils/
By looking for clues on every Web page of a new tool, you can eventually reach 10+ new NirSoft tools !
Be aware that the clues gradually become harder and more tricky and require different abilities (For example: Using NirSoft tools to decrypt encrypted information), so it’s possible that at some point you won’t be able to find the next tool. Also, in some of the clues there is an hint of TV shows and movies (Just for fun…).
Share the links with others !
If you find the URL of one or more tools, you are welcomed to publish the links in any way you like – Facebook, Twitter, Forums, Blog, YouTube, and so on
(except of publishing the links in comments to this Blog post… )
Maybe you’ll be the first one in the world who write about the new tools before anyone else !