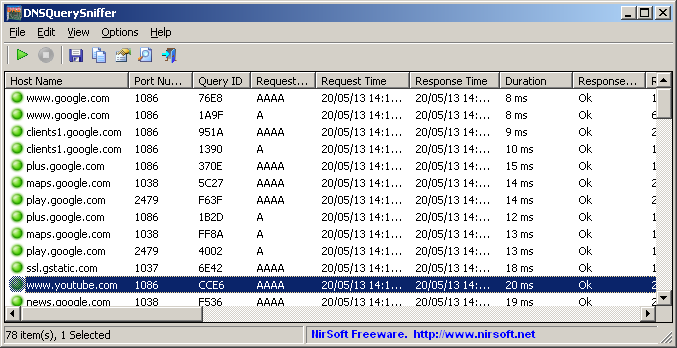
DNSQuerySniffer is a new network sniffer utility that shows the DNS queries sent on your system. For every DNS query, the following information is displayed: Host Name, Port Number, Query ID, Request Type (A, AAAA, NS, MX, and so on), Request Time, Response Time, Duration, Response Code, Number of records, and the content of the returned DNS records.
You can easily export the DNS queries information to csv/tab-delimited/xml/html file, or copy the DNS queries to the clipboard, and then paste them into Excel or other spreadsheet application.
DNSQuerySniffer works on any version of Windows, starting from Windows 2000, and up to Windows 8. Both 32-bit and 64-bit systems are supported.
You can download this new utility from this Web page.