If you recently had a power outage in your area, and you want to find out when the power was back on, there is a small trick to discover this information – by using wireless networks !
This trick only works if you live in Densely populated area with dozens of wireless access point around you, and only if the power outage was in the last few days.
Here’s a little explanation about how it works: every wireless access point has a timer that starts from zero when the router is loaded and this timer is constantly broadcasted with the access point name and other information.
The timer is also set back to zero from time to time (Depending on router model) without restarting the router, but in the short term, it’s still possible to use this timer to detect when the router was started.
When the power comes back after a power outage, all routers are loaded almost at the same time, and this time roughly represents the time that the power was back on.
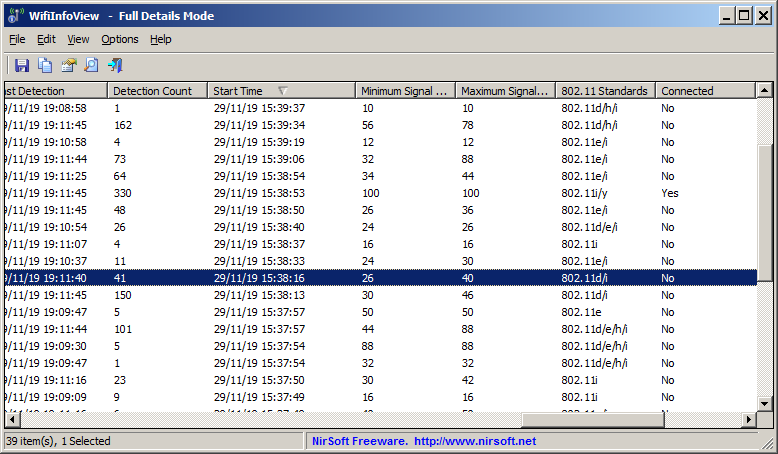
The WifiInfoView tool of NirSoft, receives the wifi timestamp of every wireless access point, calculates the time when the timer was started and displays this time under the ‘Start Time’ column.
In order to discover when power was back on, you have to click the ‘Start Time’ column header for sorting the list by the timer of every access point.
If you had a power outage recently, you should see that many access points have almost the same start time value.
In the screenshot below, which was taken a few hours after real power outage, the ‘Start Time’ of multiple routers is between 15:37 – 15:39
It means that the power was back on around 15:37.
The reason for the 2 minutes time-difference between the access points is their loading speed. In the slower routers, the timer started 2 minutes after the power was back on.