After digging more into the MsnPass.Info scam that I reported in previous posts, I found out that this scam is a only part of possibly a larger scam that may involve in collecting emails and passwords of french users.
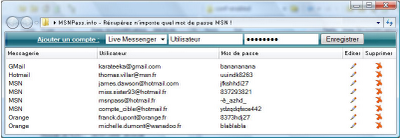
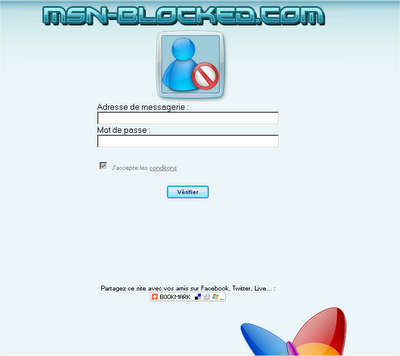
msn-blocked.com is a Web site that offers french users to find out who block their msn messenger user. In order to use this “service”, the users are required to provide their MSN user name and password.
Currently, it has at least 3 active servers: http://s601.msn-blocked.com/, http://s502.msn-blocked.com, http://s12.msn-blocked.com
There are some other addresses that already blocked by Firefox with “Reported Web Forgery!” message (For example: http://s11.msn-blocked.com), probably after users reported that it’s a phishing site.
But every time that a Web address is blocked, the scam owner simply replace it with a new server name.
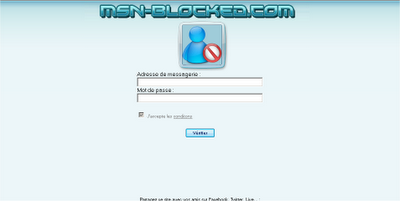
This Web site has a terms and conditions in french, so I used the ‘Google Translate’ tool for translating them to English, and that’s what they say: “The site aims to provide you with tools to identify people who you are blocked and / or removed from their list of contacts on MSN or Windows Live Messenger. In return you grant this site (MSN-blocked.com) to include your email address in mailing lists marketing.”
In other words, the Web site owner says that he collect every email entered by the user for spamming purposes.
Just for a test, I tried to create a new MSN account (I wouldn’t give my real user name/password for criminals) and use them in http://s12.msn-blocked.com/ Web site.
After I did it, The Web site showed it’s connecting to the MSN server, and than it redirected me to a page with a few french words that I don’t understand. A few seconds later, it redirected me again… to mspass.info Web site.
So after I gave my user name/password to the Web site owner, he simply offer me to buy my own utility through SMS/phone system of allopass.com.
In the beginning, both msnpass.info and msn-blocked.com were hosted in the same server, but now each of these Web site is hosted in 3 – 4 separated servers.
There are 2 other things to concern:
1. This Web site (msn-blocked.com) may also collect that passwords of each user that uses this service, and that’s really bad, especially when we already know that the owner is a thief that sell the software of others.
2. With the MSN user name/password, the Web site owner can collect the email addresses of all the contacts of the user – for spamming purposes.
But the most concerning thing in this scam is the large amount of traffic the scam owner managed to receive.
I have already seen many scam Web sites in my life, but scale of this scam is really unusual.
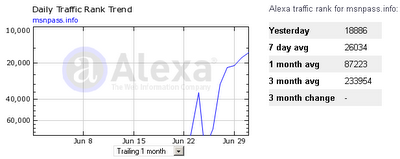
Both Alexa and radarurl.com (a widget added by scam owner to watch the number of online users) displayed exterme amount of traffic in the last
few days.
radarurl.com already removed msnpass.info and msn-blocked.com sites (Maybe because the owner of radarurl.com found out about this scam), but before they were removed, it was displaying around 100-200 online users for each server (around 1000 online users for all servers together) in the peak hours.
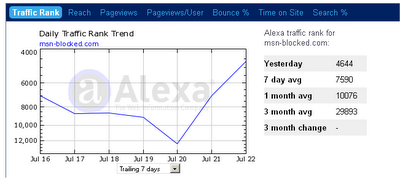
In Alexa, the traffic rank of msn-blocked.com is around 8000 in the last few days, which is very high for a Web site that established only 3 weeks ago.
Moreover, it seems that the scam owner have at least 8 dedicated servers (4 for msnpass.info and 4 for msn-blocked.com) which implies that it’s really a major scam. The scam owner wouldn’t pay for 8 dedicated servers unless there is something huge behind that.
As I already reported, I tried to contact both ovh.com hosting and the payment company (allopass.com) by email and from their Web site contact forms, but with no success.
They simply don’t answer – I don’t know if they simply don’t understand English or they don’t really care that their services are used for fraud activities.
Unfortunately, I don’t live in france and I don’t speak french, so I cannot do anything else to shut down this scam.
If you live in france and/or you can talk in french, you may try to call this ovh.com company, get to the right department, and tell them about scam of msn-blocked.com and msnpass.info.
If no one will do something about this scam, these criminals will continue to collect more and more msn emails/passwords and to make money from selling my software.
In the end, they’ll have a nice amount of money in the bank, and a large user/password database that will allow them to do many other terrible things.
Finally, here’s a small explanation about how these Web sites get all the traffic:
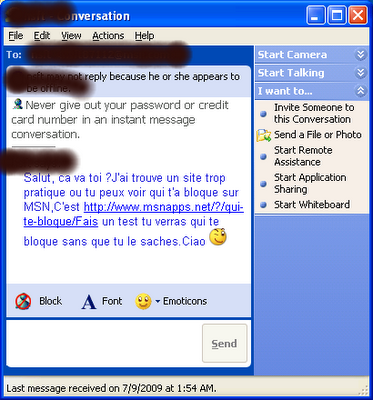
Each time that a use put his user name and password into msn-blocked.com, this Web site send a live message in french to all the contacts of the user:
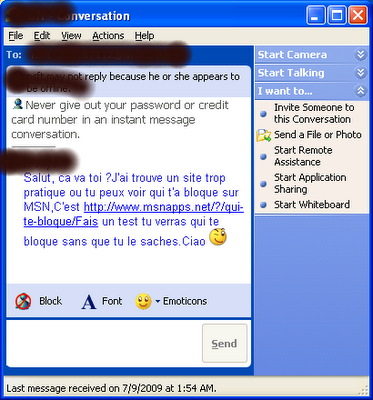
The message is sent in the name of the user that gave his user name/password, and invite all contacts to check the Web sites of MsnPass.Info or msn-blocked.com
The users that receive this message think that it as came from their messenger friend, and thus many of them browse into this Web site, login with their user/password, and cause this viral spreading to continue.