A few days ago, I reported that Allopass company decided to close the account of msnpass.info scam. So it seems that they simply lied to me.
After a few days, I saw that msnpass.info Web site is still very active, so I contacted Allopass again, and now their representative says that they are not going to close the account.
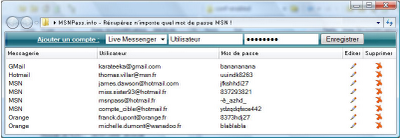
The reason: The owner of msnpass.info told them that msnpass.info sell a software developed by msnpass.info team, and this Web site doesn’t sell the utilities of NirSoft at all.
This is probably the reason for the screenshot change, that I reported a few days ago.
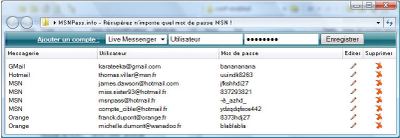
The owner of msnpass.info created a fake screenshot of a software that doesn’t really exist, and told the Allopass company that msnpass.info sell the software shown in the screenshot, which doesn’t look like the MessenPass utility of NirSoft.
But according to reports that I received in the last days from 2 people that fell into msnpass.info scam, after users pay through the payment system of Allopass, they are still sent to download my MessenPass and Mail PassView utilities.
The fake screenshot in the landing page of msnpass.info was just created to give Allopass a good excuse for not closing the account.
The sad fact is – Both msnpass.info and Allopass company have interest of keeping msnpass.info account open and to continue making a lots of money from this nasty scam.
In the last few weeks, I was in contact with a few employees of Allopass company regarding this scam, and in all this time, they just wasted my time and protected the side of the criminals.
Instead of suspending the account of msnpass.info and require this Web site owner to stop the nasty MSN spamming activities and to stop selling the software of others,
Allopass simply sent my complaint to msnpass.info owner. msnpass.info owner answered them that he sell his own software and not my software, and Allopass simply accepted this answer, and decided to keep the account open.
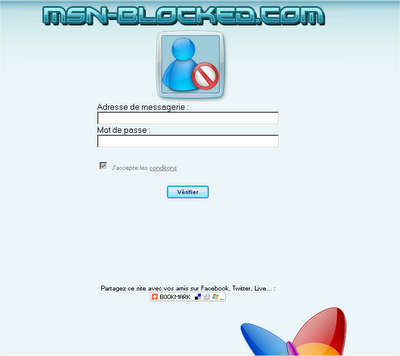
Just to remind you again – msnpass.info and msn-blocked.com are a pair of scam Web sites in french that use very nasty way to get a large amount of traffic and… money.
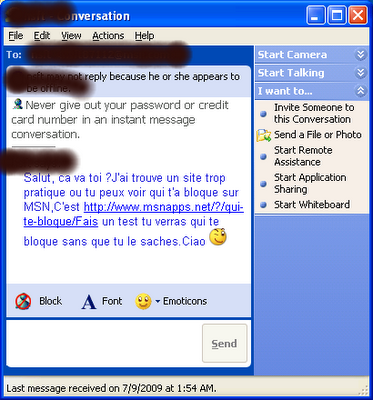
The first one, msn-blocked.com – asks innocent users to type their MSN user/password, and then floods all their contacts with fake instant messages that invite them to join msn-blocked Web site, and enter their user/password too.
The second one, msnpass.info – offer the users of msn-blocked.com to purchase the MessenPass utility of NirSoft through the SMS payment system of allopass.com, misleading french users that don’t know that this utility is available for free at www.nirsoft.net.
For more information about how this scam works, read this post.
msn-blocked.com blocked by Firefox, so other domains are used
Due to complains of many users about msn-blocked Web site, Firefox and Google blocked this domain for ‘Reported Web Forgery’.
So the owner of this scam started to redirect Firefox users to other domains like msn-block.info, msn-blocking.com, msn-check.info, and possibly others.
msn-block.info and msn-blocking.com domains are already completely blocked by Firefox too, while msn-check.info is only partly blocked.
So for, Firefox/Google are the only good side in this world that do something against this scam.
I already reported about this scam to Microsoft (for MSN Messenger abuse), to GoDaddy (The domain registrar), to Domains By Proxy (the privacy protection company), to EURO-WEB Servers renting (the current hosting company), and to some other organizations that handle these kind of scams. So far, there is no any action from any of them.