FirefoxDownloadsView is a new utility that displays the list of the latest files that you downloaded with Firefox. For every download record, the following information is displayed: Download URL, Download Filename (with full path), Referrer, MIME Type, File Size, Start/End Time, Download Duration, and Average Download Speed.
You can easily select one or more downloads, and then save the list into xml/html/text/csv file or copy the downloads information to the clipboard and paste it into Excel or other spreadsheet application. You can also copy (With Explorer Copy – Ctrl+E) and paste the downloads list into HashMyFiles utility, in order to check the MD5/SHA1 hashes of the downloaded files.
For more information about this utility, click here.
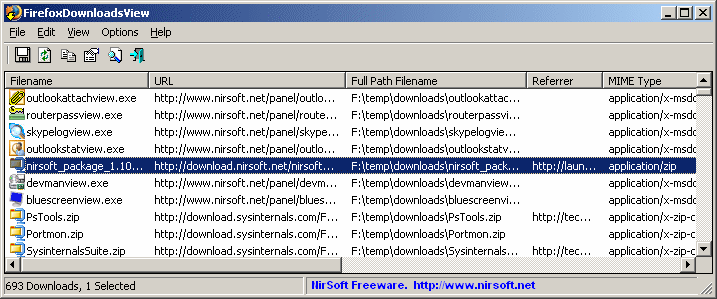
FirefoxDownloadsView
Posted by NirSoft on February 15, 2011 at 1:34 pm under Utilities Update.
Comment on this post.
DriveLetterView is a new utility that allows you to view the list of all drive letter assignments in your system, including local drives, remote network drives, CD/DVD drives, and USB drives – even if they are not currently plugged.
It also allows you to easily change a drive letter of USB devices and remote network shares, as well as to delete a drive letter of USB device that is not plugged, and to export the list of all drive letters into text/csv/html/xml file.
For more information about this utility, click here.
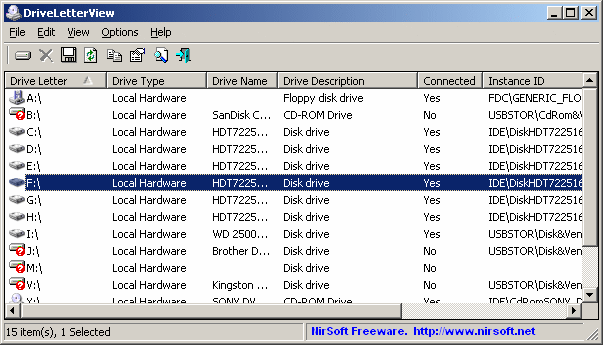
DriveLetterView
Posted by NirSoft on February 15, 2011 at 1:33 pm under Utilities Update.
Comment on this post.
2 new console applications (Command-Prompt) were added to NirSoft Web sites:
- AltStreamDump: This utility is the console version of the AlternateStreamView utility. it dumps the list of NTFS alternate streams found in the current directory or in any other directory that you choose.
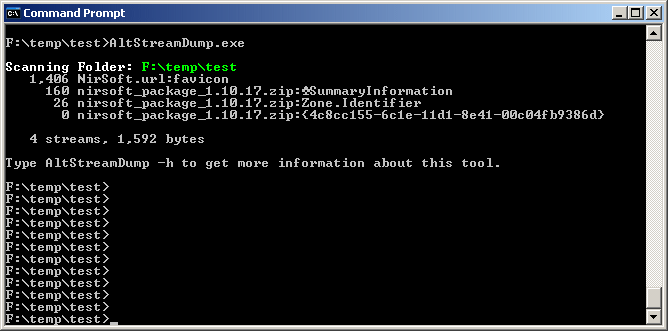
AltsSreamTump
- WirelessKeyDump: This utility is the console version of the WirelessKeyView utility. it dumps the list of all wireless keys stored by the wireless networks module of Windows operating system.
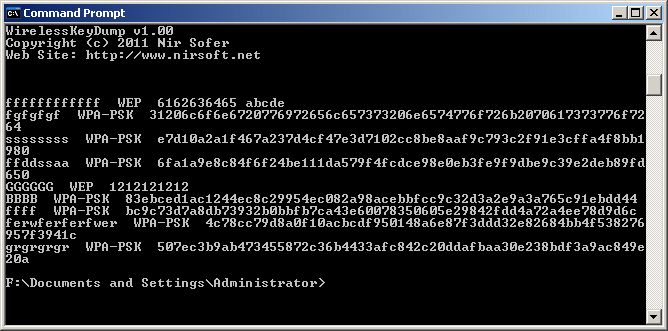
WirelessKeyDump
Posted by NirSoft on February 15, 2011 at 1:32 pm under Utilities Update.
2 Comments.
In the beta version of Firefox 4, there are some changes inside the cache files structure that caused to MozillaCacheView and VideoCacheView utilities to work improperly with it. In the new versions of these utilities, I made a few changes, so they’ll also be able to read properly the cache files of Firefox 4 Beta.
Posted by NirSoft on February 6, 2011 at 11:22 am under Utilities Update.
2 Comments.
OutlookAttachView now allows you to search Outlook attachments only in the folders that you choose, instead of scanning the entire mailbox of Outlook.
Currently, there is no user interface to choose the desired Outlook folders (It’s possible that I’ll add ‘Choose Folders’ window in future versions), so you have to manually type the list of folders that you wish to scan, as comma-delimited list.
You can type only the folder name, for example: Inbox, Sent Items, and so on. If you type ‘Inbox’ as the folder name and you have multiple Inbox folders in your Outlook profile, all your Inbox folders will be scanned.
If you want to scan only a specific Outlook folder, you have to type the entire folder path, for example: Personal Folders\Inbox
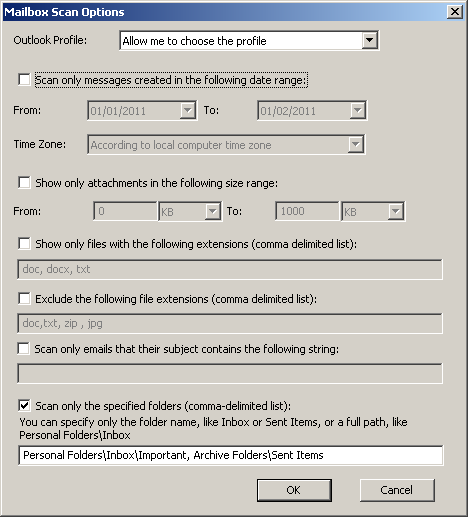
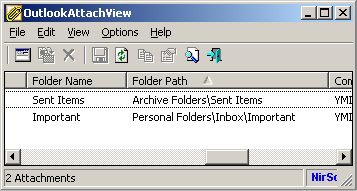
If you are not sure what is the exact folder path, you can simply make a full attachments scan, and then copy the folder path from the ‘Folder Path’ column:
Posted by NirSoft on January 29, 2011 at 10:21 am under Utilities Update.
Comment on this post.
The new versions of WhoisThisDomain and DNSDataView utilities allow you to type domain names which contain non-English characters (internationalized domain names).
when you type a domain with non-English characters, it automatically converted to its Ascii form (Which looks like xn--aaaaaa.com) before sending it to the Whois/DNS server.
However, be aware that I currently use the internal IDN support provided by Windows operating system, which was added starting from Windows XP with service pack 2,
so this new feature may not work on systems prior to XP/SP2.
You can check whether your Windows OS supports IDN by searching for normaliz.dll inside your system32 directory.
If this file exists, it means that your system has IDN support.
Posted by NirSoft on January 28, 2011 at 1:13 pm under Uncategorized.
Comment on this post.
I originally planned to start the first day of this new year with “Happy New Year” greeting for my users (Which I added in the title of this post) and a list of new utilities that will be released in the incoming year.
However, because there are already many existing utilities that I have to update, the planning and development process of new utilities is much slower than before.
Currently, there are 2 new utilities that are in development process and other ideas for utilities that are still in ‘planned’ status and I still don’t know whether they are going to be created.
Here’s the list of the 2 new utilities and some of the ‘planned’ utilities:
- WhatIsHang (In development): Sometimes, a Windows software hangs, the user interface doesn’t respond anymore, and you cannot find out what is cause for the problem (In fact, even my own utilities may hang in some circumstances).
This new utility will try to detect the software that is currently hang, and it’ll display some information that may allow the user to understand what exactly cause the software to hang.
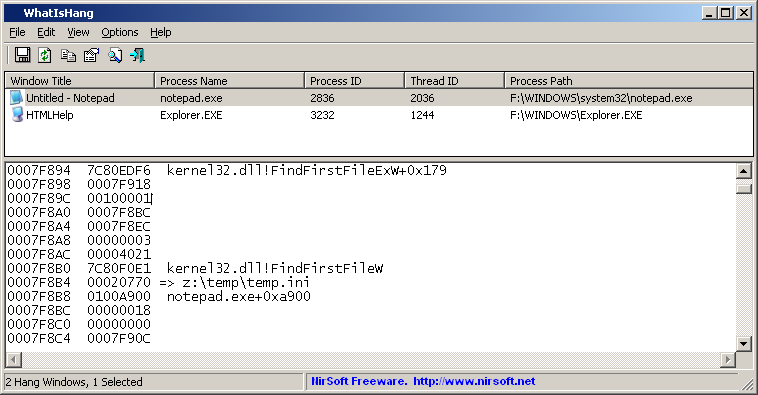
WhatIsHang
In the above example, I tried to open Notepad with a file on a network drive that cannot be accessed (z:\temp\temp.ini) and Notepad stopped responding. The prototype of WhatIsHang detected that notepad doesn’t respond, and displayed the ‘z:\temp\temp.ini’ filename string that was found in the stack, which is really the cause of the problem.
I’m also considering to create a similar utility for detecting application crash problems.
- Password Security Scanner (In development): As you probably know, I already have some unique utilities that can extract passwords that are stored by the operating system and other applications. As opposed to all my other tools, this utility won’t display the passwords at all, but instead, it’ll display general information about the security of the password: Password Length, Password Strength, Number of numeric/lowercase/uppercase characters, and more…
The idea behind this tool is to allow one person to check whether other people (family members, friends, or employees) use passwords that are secured enough (and warn them if they are not), but without having the ethics problem of watching the passwords of others.
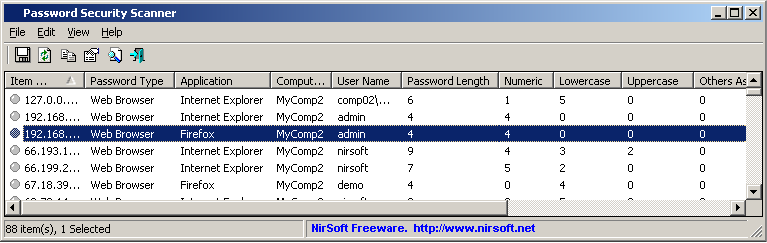
Password Security Scanner
- Network statistics utility (planned): Many people requested to add more information into my CurrPorts utility, like number of sent/received packets, total packets size, and so on. However, this information cannot be added without a using device driver. Also, CurrPorts is only designed to display TCP/UDP information, while there are other types of network packets that won’t be displayed by CurrPorts.The new network statistics utility (If I’ll really create it) will capture every packet on your network adapter with WinPCap driver or with Microsoft Network Monitor Driver. it’ll detect the protocol, addresses, and ports of the packet, and then it’ll be updated in the statistics table that will display the number of packets, data size, data speed, and other information for every protocol/network address.
- Wireless networks statistics utility (planned): A utility that will capture all wireless raw packets while the wireless card is in ‘Monitor Mode’ and will display general statistics about the wireless activity in your area, including number of packets, packets size, packets encryption, and so on.
The main problem with creating this utility is that ‘Monitor Mode’ is only supported starting from Windows 7/Vista (with Microsoft Network Monitor Driver), so if I develop it, many Windows XP users won’t be able to use it. And… as far as I know, WinPCap driver cannot capture raw wireless packets under Windows, unless you use their AirPcap product, which is very expensive.
- Simple Network Inventory Tool (planned): a simple tool that will collect basic hardware/software information from multiple computer on your network, like disk size, memory, processor name, Windows service pack/version, IE version, Firefox version, and so on… and it’ll display it in a simple flat table to easily view and compare the software/hardware that you currently have on your computers.
- Password Recovery from external drive (planned): I constantly get requests from people that their old drive cannot boot anymore and they want to extract their passwords from it. Some of my password recovery tools can already do that, and others cannot.
I’m considering to create one tool that will be able to extract most types of passwords from external drive, but… because Microsoft made a significant change in their password encryption starting from Windows 7, my current code cannot extract the passwords of Windows 7 from extenal drive, and upgrading my code to work with Windows 7 might be a long process.
Posted by NirSoft on January 1, 2011 at 1:04 pm under Utilities Update.
8 Comments.
BulletsPassView is a new utility that reveals the passwords stored behind the bullets on any version of Windows, starting from Windows 2000, and up to Windows 7/Vista/2008.
This utility is the successor of my old Asterisk Logger utility, which doesn’t work on Windows 7/Vista/2008 and has some other limitations.
BulletsPassView also has some other advantages over the old Asterisk Logger tool:
- BulletsPassView doesn’t reveal the password inside the password text-box itself. The password is only displayed in the main window of BulletsPassView, while the password text-box continues to display bullets.
- BulletsPassView also reveals the passwords stored in the password text-box of Internet Explorer.
- BulletsPassView supports command-line options to save the current opened password boxes into text/html/csv/xml file.
- BulletsPassView is a unicode application, which insures that passwords with non-English characters will be extracted properly.
You can download the new BulletsPassView utility from here.
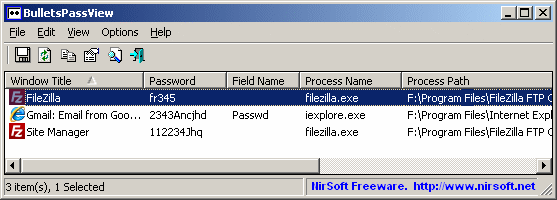
BulletsPassView
Posted by NirSoft on December 2, 2010 at 2:46 am under Utilities Update.
Comment on this post.
MyEventViewer utility has a new ‘Auto Refresh’ feature that allows you to watch newly created events at the moment they are created, without the need to refresh the events list.
You can activate the ‘Auto Refresh’ mode from ‘Auto Refresh’ option under the Options menu, as displayed in the following screenshot. You can choose to check for new events every 1, 3, 5, or 10 seconds.
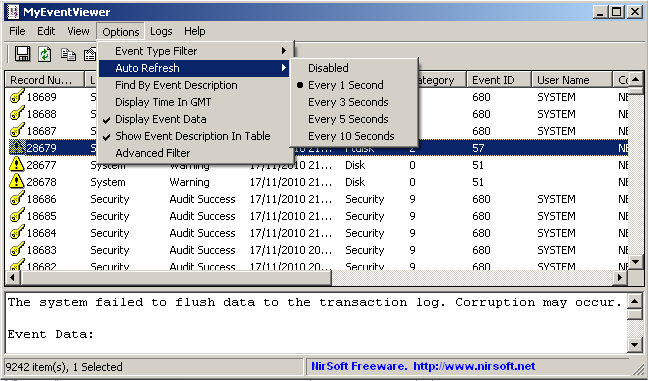
Auto Refresh
You can find the latest version of MyEventViewer utility in this page.
Posted by NirSoft on November 18, 2010 at 1:51 am under Utilities Update.
4 Comments.
A few months ago, I released a new version of both SmartSniff and SniffPass with support for using them with Microsoft Network Monitor 3.x
In the release details, I also specified that ‘Wifi Monitor Mode’ button was added for using ‘Monitor Mode’ under Windows Vista/7/2008, but without giving extensive explanation about how to use this feature. So in this blog post, I’ll add more details about this ‘Wifi Monitor Mode’ and how to use it on SmartSniff and SniffPass.
When a wireless network card enters into a ‘Monitor Mode’, it listens to specific channel that you choose and captures all the packets that are sent by wireless networks on your area in the specific channel that you selected. If the wireless network that sent the packet is unsecured, SmartSniff and SniffPass will be able to show you the packets data.
Before I start to explain you how to use this mode, here’s the system requirements for using ‘Monitor Mode’:
- Unfortunately, this mode is only supported on Windows Vista, Windows 7, and Windows Server 2008. Windows XP is not supported.
- Both the network card and the device driver must support this mode. I currently don’t have a list network cards that support this mode under Windows. However, if you manage to get your card into monitor mode, it’ll be nice if you post your card model as comment to this Blog post.
Also, be aware that according to Microsoft, some Wifi drivers may cause a system crash when entering into monitor mode.
Finally, here’s the instructions for using ‘Wifi Monitor Mode’ with SmartSniff and SniffPass:
- First, download and install the latest version of Microsoft Network Monitor 3.x if it’s not already installed on your system.
- Run SmartSniff if you want to capture general TCP data or SniffPass if you only want to capture passwords. Be aware that SniffPass can only capture passwords that are not encrypted. Most Web sites and services of large companies use SSL to encrypt the passwords, and thus SniffPass cannot capture them.
- Go to the ‘Capture Options’ window (F9), choose ‘Network Monitor Driver 3.x’ as a capture method, and then click the ‘Wifi Monitor Mode’ button.
- In the opened ‘Wifi Scanning Options’ window, choose the right wireless card (in most cases you should have only one) and then check the ‘Switch to Monitor Mode’ option.
- You can now select to scan a single channel or to switch between multiple channels every x milliseconds. After you selected the desired channels, click the Apply button.
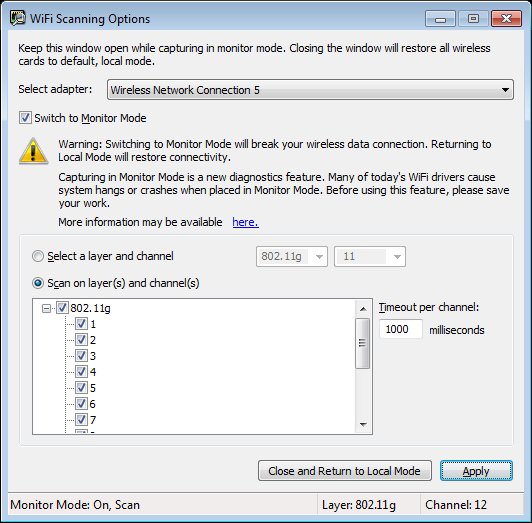
Wifi Scanning Options
- The most important thing: Leave this window opened !
When you close this window, the network card will exit from monitor mode and it’ll return back to its normal state.
- In ‘Capture Options’ window of SmartSniff/SniffPass – select the right wireless card and then press the ‘Ok’ .
- Finally, press F5 to start the capture. If you have any active unsecured networks in your area, you’ll be able to see the captured data.
- After you finish, close the ‘Wifi Scanning Options’ window, so your wireless card will return back to normal.
The information in this article is provided for educational purposes only and for making people aware of the risks of using unsecured wireless networks. it’s not intended to be used for any illegal activity.
Posted by NirSoft on November 8, 2010 at 3:55 am under NirSoft Tips.
35 Comments.











