In the last few weeks, I added support for recovering passwords from external hard drive contains the most recent versions of Windows (Windows 10, Windows 8, Windows 7) for some of the NirSoft Password-Recovery tools, including IE PassView, ChromePass, Network Password Recovery, and WirelessKeyView.
Until now there was only support for reading external drive passwords of Windows XP or Windows Vista and I had to do a very intensive reverse engineering in order to upgrade my DPAPI decryption code to work with Windows 7 and newer systems.
In addition to the upgrade of existing tools, there are also a few new utilities in development process that are specifically designed to extract passwords from external hard drive.
The combination of external drive support and the shadow copies of Windows also allows you to recover old passwords from a few weeks ago instead of the current passwords stored on your system.
Here’s an example for using the external drive support to recover previous passwords stored in your system:
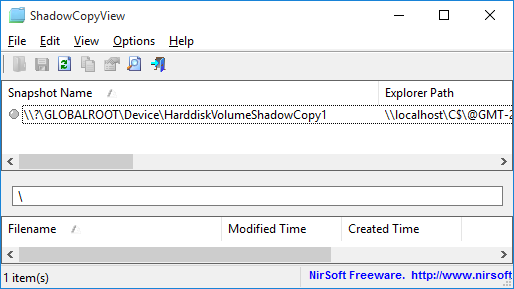
First… You have to run the ShadowCopyView utility to check the current shadow copies you have on your system.
If the main window of ShadowCopyView is empty, it means that there are no shadow copies and thus you cannot recover old passwords stored in your system.
In the following sample screenshot, you can see that there is a single shadow copy and its path is \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1
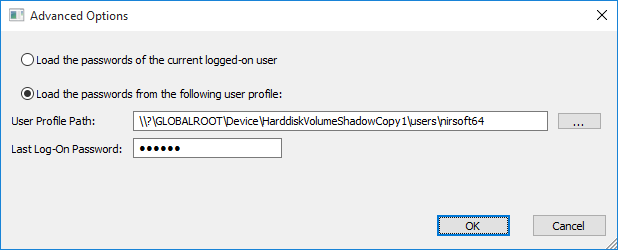
Now… Lets say that you accidentally deleted the passwords stored by Internet Explorer and now you want to recover them, so in IE PassView tool you should go to the ‘Advanced Options’ window (F8) and , choose the ‘Load the passwords from the following user profile’ option, and then type the shadow copy path of your user profile.
For example, if your user profile is stored in c:\users\nirsoft64 and the shadow copy path is \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1 then the correct path that you have to type is \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\users\nirsoft64 :
You also have to type the logon password of this user profile, because the logon password is needed to decrypt the passwords.
Assuming that you type the correct user profile path and logon password, IE PassView will decrypt the passwords stored by IE in the date that the shadow copy was created.
You can also use the same technique with the other tools that have external drive support (ChromePass, Network Password Recovery, WirelessKeyView, Dialpass )
Be aware that like any password-recovery tool, these tools trigger warnings and alerts in many Antivirus programs and your Antivirus software, firewall, or even your Web browser may block you from downloading them.

Tony4219 says:
Thank you for adding external drive supports!!! Many times support people have to recover info from ‘dead’ systems or improperly working systems (Win10 upgraded from Win8 or Win7 that had Windows ‘remember my passwords’ for the last bunch of YEARS) .
September 9, 2016, 8:15 amJerry Edwards says:
Thanks for this post Nir. If I understand this correctly, it sounds like quite a flaw in the windows design, that passwords can actually be found like this? Handy at times yes, but the risk factor seems quite high…
November 15, 2016, 1:42 pm