NTFS system has a feature that allows to add multiple streams in addition to the main file stream. When you open or view the file, only the main file stream is visible, while other additional streams are hidden from the user.
Here’s 3 examples of alternate streams usage in Windows operating system:
- Favorites of Internet Explorer: When You add a Web site link into your ‘Favorites’, a .url file containing the url and description is created. However, if the Web site also have an icon (favicon), the icon is saved as alternate stream for the same url file. The stream name of the icon is :favicon:$DATA
- Downloaded files of Internet Explorer: When you download and save a file with Internet Explorer, it automatically add a zone information for the saved file. This zone information is used for identifying the file as downloaded file from the Internet. The stream name in this case is :Zone.Identifier:$DATA
- Summary information of files: When you right-click on a file in Explorer and go to the ‘Summary’ tab, you can add summary information for the file, like title, subject, author, and so on. This summary information is also saved into alternate stream. The stream name in this case is SummaryInformation:$DATA.
In addition to the legitimate usage of alternate streams, this technique may also be used by Viruses/Trojans/Spywares for saving data and hiding it from the user.
AlternateStreamView is a new GUI tool that allows you to easily scan your NTFS drive, and find all hidden alternate streams stored in the file system. After scanning and finding the alternate streams, you can extract these streams into the specified folder, delete unwanted streams, or save the streams list into text/html/csv/xml file.
For more information and download link, click here
Posted by NirSoft on February 12, 2009 at 3:27 am under Utilities Update.
1 Comment.
MozillaCacheView and OperaCacheView:
- Added support for cache filter. (Display only URLs which contain the specified filter strings)
RegScanner:
- Export Selected Items – String values are now exported as strings and DWord values are now exported as DWords. (In previous versions they exported as binary)
- Fixed bug: When using ‘Export Selected Items’ more than once, the first key was missed
FavoritesView:
- Added support for command-line.
- Added support for saving as .csv file.
- The settings are not saved to .cfg file instead of the Registry.
Posted by NirSoft on February 12, 2009 at 3:20 am under Utilities Update.
Comment on this post.
- MyLastSearch: Added filter by Web browser (in Advanced Options)
- InsideClipboard: Added support for saving and loading as Windows .clp file. You can use it from the user interface or from command-line.
- IECacheView: Added support for cache filter. (Display only URLs which contain the specified filter strings)
- BluetoothView: New Option: Execute a command when a new Bluetooth device is detected. (In ‘Advanced Options’)
- NirCmd:
- New actions for clipboard command – loadclp and saveclp (load/save in Windows .clp format)
- New command: setprocessaffinity
Posted by NirSoft on February 3, 2009 at 3:01 pm under Utilities Update.
3 Comments.
- SysExporter: Added support for drag And drop feature – Allows you to easily locate the desired window simply by dragging the target icon from the SysExporter toolbar into the window that you need to grab the data.
- RegScanner: New option: Show found items during the scan process
- Mail PassView: Added support for Windows Live Mail.
- PasswordFox: Added new option in ‘Select Folders’ dialog-box: Remember the folder settings in the next time that you use PasswordFox.
- Dialupass: Dialupass now also locate the phonebook file even when the ‘Application Data’ folder is in non-english language.
- CurrPorts:
- Added new column: Window Title (The window title of the process)
- Added ‘Cleal All Filters’ option.
- Added ‘Include Selected Processes In Filters’ option. Allows you to easily filter by selected processes.
Posted by NirSoft on January 26, 2009 at 3:28 pm under Utilities Update.
2 Comments.
In the last few days, I received a lots of emails with “IKEA’s New Planning Software” in the subject:
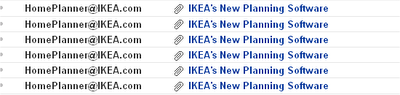
This email offers a new Home Planner software from IKEA , and ask the user to follow the instructions in the attached zip file. But the attached file contains a Virus that probably continues to spread this “New Planning Software” message to more and more users.
The email looks like this one:
From: HomePlanner@IKEA.com
Subject: IKEA’s New Planning Software
From: “HomePlanner@IKEA.com”
Attachment: ikea.zip (347KB)
Body:
IKEA has a Fantastic new FREE tool for home decorating.
Introducing our Home Planner software which allows you to plan your home in a 3D environment.
Simply follow the instructions in the attachment and start planning your dream home today.
Posted by NirSoft on January 15, 2009 at 2:16 pm under Internet Scams.
Comment on this post.
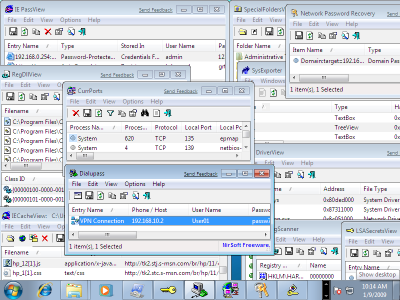
I just tested a few of my utilities on Windows 7 Beta.
The test included IE PassView, IECacheView, Network Password Recovery, SysExporter, RegScanner, Dialupass, CurrPorts, DriverView, LSASecretsView, and more.
It seems that all tested utilities work fine under Windows 7, as you can see in the following screenshot:
Posted by NirSoft on January 10, 2009 at 2:18 am under Uncategorized.
Comment on this post.
SiteShoter:
- Added new options: ‘Save Config’ and ‘Load Config’
- Added new command-line option: /LoadConfig – Start SiteShoter with the specified config file.
- Added new command-line option: /RunConfig – Take a screenshot according to the specified config file, without displaying any UI.
ResourcesExtract:
- Added new options: ‘Save Config’ and ‘Load Config’
- Added new command-line option: /LoadConfig – Start ResourcesExtract with the specified config file.
- Added new command-line option: /RunConfig – Extract resources according to the specified config file, without user interface.
RegDllView:
- Added new option: ‘Create .Reg File For Deleting Entries’ – Allows you to create a .reg file that will remove all entries of the selected registered files when you run it. This option can be useful if you want to clean the same registered files in multiple machines.
- Added more accelerator keys.
- Fixed the focus problem after using the unregister/delete options.
Dialupass:
- Dialupass completely rewritten, and the new version contains all the current NirSoft standards, including the ability to translate to other languages.
- Added support for recovering dialup passwords from external instance of Windows 2000/XP/2003. This feature can be useful if you have a dead operating system that cannot boot anymore.
- Added support for setting dialup user/password from command-line (/setpass)
NirCmd:
- New commands: waitprocess, setprocesspriority, qboxtop, qboxcomtop.
- New action in clipboard command: copyimage (Copy image file to the clipboard)
OpenedFilesView:
- New option: Bring process to front.
- Added more accelerator keys.
Posted by NirSoft on January 4, 2009 at 1:50 pm under Utilities Update.
1 Comment.
Since I started to collect general statistics about Web browser usage of nirsoft.net, 4 years ago, there was a gradual increase in usage of Firefox, while the usage of Internet Explorer gradually decreased.
According to statistics of the last month (December 2008), 29.2% of nirsoft.net visitors use Firefox as thier Web browser, while 55.8% of visitors use Internet Explorer.
For more nirsoft.net statistics, click here.
Posted by NirSoft on January 1, 2009 at 2:10 pm under Uncategorized.
2 Comments.
In the last few weeks, some virus distributors try to exploit the holiday season in order to spread Viruses more easily. The viruses are attached to email messages that offer coupons or special offers for Christmas.
The first 2 ‘Christmas Virus Messages’ already appeared in the beginning of december and these emails identified themselves as originating from Coca Cola and Mcdonalds.
Now there are 3 new messages which identified themselves as originating from Symantec, British Airways and Jack Daniel’s.
As my email address is pretty popular, I received dozens of these emails together with other junk, as you can see in the following screenshot:
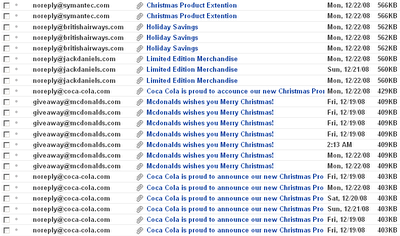
All these emails instruct the user to open the attached file, which contain a Virus that probably continues to send these emails to more and more people.
Here’s the details of all 5 Christmas Virus Messages:
- Symantec
Subject: Christmas Product Extention
From: “noreply@symantec.com”
Attachment: product-extention.zip
Message Body:
This holiday season Synamtec is rewarding our valued customers by extending your products protection period by six months.
Follow the instrustions in the attachment to receive your extra protection and have a wonderful Christmas!
Offer valid until midnight 31st January 2008.
- British Airways
Subject: Holiday Savings
From: “noreply@britishairways.com”
Attachment: britishairways-coupon.zip
Message Body:
British Airways is offering fantastic deals this festive season. Check your attached coupon and book online today for an amazing holiday!
- Jack Daniel’s:
Subject: Limited Edition Merchandise
From: “noreply@jackdaniels.com”
Attachment: jackdaniels-coupon.zip
Message Body:
Have yourself a Merry Christmas with Jack Daniel’s.
Print the coupon and head for your local outlet
for limited edition merchandise.
- Coca Cola
Subject: Coca Cola is proud to announce our new Christmas Promotion
From: “noreply@coca-cola.com”
Attachment: promotion.zip
Message Body:
Coca Cola is proud to announce our new Christmas Promotion.
December, 2008
Play our fantastic new online game for your chance to WIN a trip to the Bahamas and get all Coca Cola drinks for free in the rest of your life. See the attachment for details.
- Mcdonalds
Subject: Mcdonalds wishes you Merry Christmas!
From: “giveaway@mcdonalds.com”
Attachment: coupon.zip
Message Body:
McDonald’s is proud to present our latest discount menu.
Simply print the coupon from this Email and head to your local McDonald’s for FREE giveaways and AWESOME savings.
Posted by NirSoft on December 23, 2008 at 3:28 am under Internet Scams.
1 Comment.
When you run operating system inside a Virtual PC, the current date/time is automatically taken from the host operating system.
This feature is useful for most cases, but sometimes you may want to run the guest operating system with specific date and time, instead of the current date/time.
You can do that simply by changing the date/time of your computer, but this change will also affect the other programs running in the same machine.
To change only the date/time of the guest operating system, you can use one of the following methods:
- Manually change the .vmc file:
The .vmc files contain the configuration of each virtual machine and are usually located under [User Profile]\My Documents\My Virtual Machines\[Virtual Machine Name]
You have to make 2 changes in the right .vmc file:
A. Disable the time synchronization:
Under the following mouse configuration:
<mouse>
<allow type=”boolean”>true</allow>
</mouse>
Add this:
<components>
<host_time_sync>
<enabled type=”boolean”>false</enabled>
</host_time_sync>
</components>
B. Set the desired date/time:
You have to find the time_bytes value inside the .vmc file, which looks like this one:
<time_bytes type=”bytes”>27003200110001201008</time_bytes>
After finding it, set the desired date/time value according to the following specification:
Digits 1 – 2 contain the seconds value.
Digits 5 – 6 contain the minutes value.
Digits 9 – 10 contain the hours value.
Digits 15 – 16 contain the day value.
Digits 17 – 18 contain the month value.
Digits 19 – 20 contain the year value.
In the above example, the date/time value is 11:32:27, 20/10/2008
After making the above 2 changes, save the .vmc file, and the guest operating system will start in the same date/time that you set in the time_bytes value.
- By using RunAsDate utility:
In order to use this method, download and run the RunAsDate utility, choose the desired date/time, and select the path of the Virtual PC application, (It should be something like C:\Program Files\Microsoft Virtual PC\Virtual PC.exe) and then click the ‘Run’ button to start running the Virtual PC application. If Virtual PC is already running in your computer, you should close it before starting the new one.
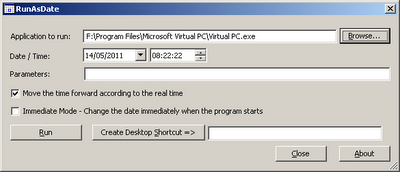
When you run the Virtual PC application within RunAsDate utility, all the guest operating systems that you run from it will automatically use the date/time that you set with RunAsDate utility, instead of the real date/time of your computer.
If you successfully used one of the above methods, you should have a running guest operating system with the date/time that you chose, while the computer’s date/time continues to run normally:
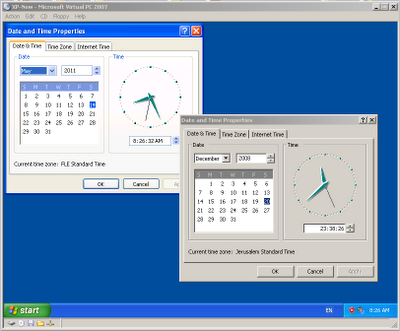
Posted by NirSoft on December 21, 2008 at 4:27 am under NirSoft Tips.
4 Comments.





