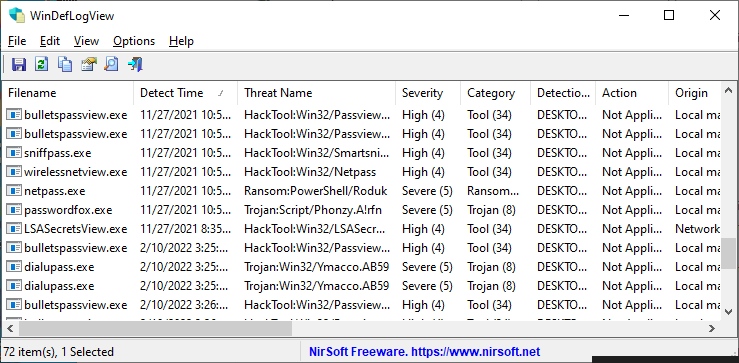
WinDefLogView is a new tool for Windows 10 and Windows 11 that reads the event log of Windows Defender (Microsoft-Windows-Windows Defender/Operational) and displays a log of threats detected by Windows Defender on your system. For every log line, the following information is displayed: Detect Time, Filename, Threat Name, Severity, Category, Detection User, Action, Origin, and more…
WinDefLogView allows you to load the detected threats log from your local system, from one or more remote computers on your network, and from external drive plugged to your computer
You can download the new WinDefLogView tool from this Web page.

Visitor says:
Speaking of threats, a malware deployer is using a .me TLD version of your domain name to host a CobaltStrike command and control server. (It’s a little puzzling to me why they used such impersonation for the C&C server address, though.) I noticed this while reading on the tech news site “Bleeping Computer” the article “Fake antivirus updates used to deploy Cobalt Strike in Ukraine” (March 14, 2022). (Viewers of this post, please don’t try out the .me address yourself; leave that to security researchers.)
March 15, 2022, 12:22 pmCarlos says:
When running this utility on my Windows 10 Pro ENG is doesn’t show up anything (an empty table) although my Windows Defender Protection History lists quite a few Low PUPs. I’ve tried Data Source: “The System” but also “External Folder” (C:\Windows\System32\winevt\Logs)
March 25, 2022, 11:46 amALso tried running as Admin.