A few years ago, I wrote a Blog post about false positive problems that I have in many of my tools, and I received many responses from users and developers that experience the same problem.
Today the false positive issues still exist, but it seems that people are more aware to the false positive problems, because I get less complaints about virus alerts in my software than what I have gotten in the past.
Some of my tools have 2 different builds – one for using on 32-bit systems and one for using on 64-bit systems.
WirelessKeyView is one of these tools that is available in 2 builds – 32-bit and 64-bit. Both 32-bit and 64-bit builds of WirelessKeyView are compiled with exactly the same code and the same compiler options, and naturally they also do exactly the same actions. The only reason for creating the 64-bit build is because WirelessKeyView injects code into a system process in order to get the wireless keys, and 32-bit process cannot execute code on 64-bit process.
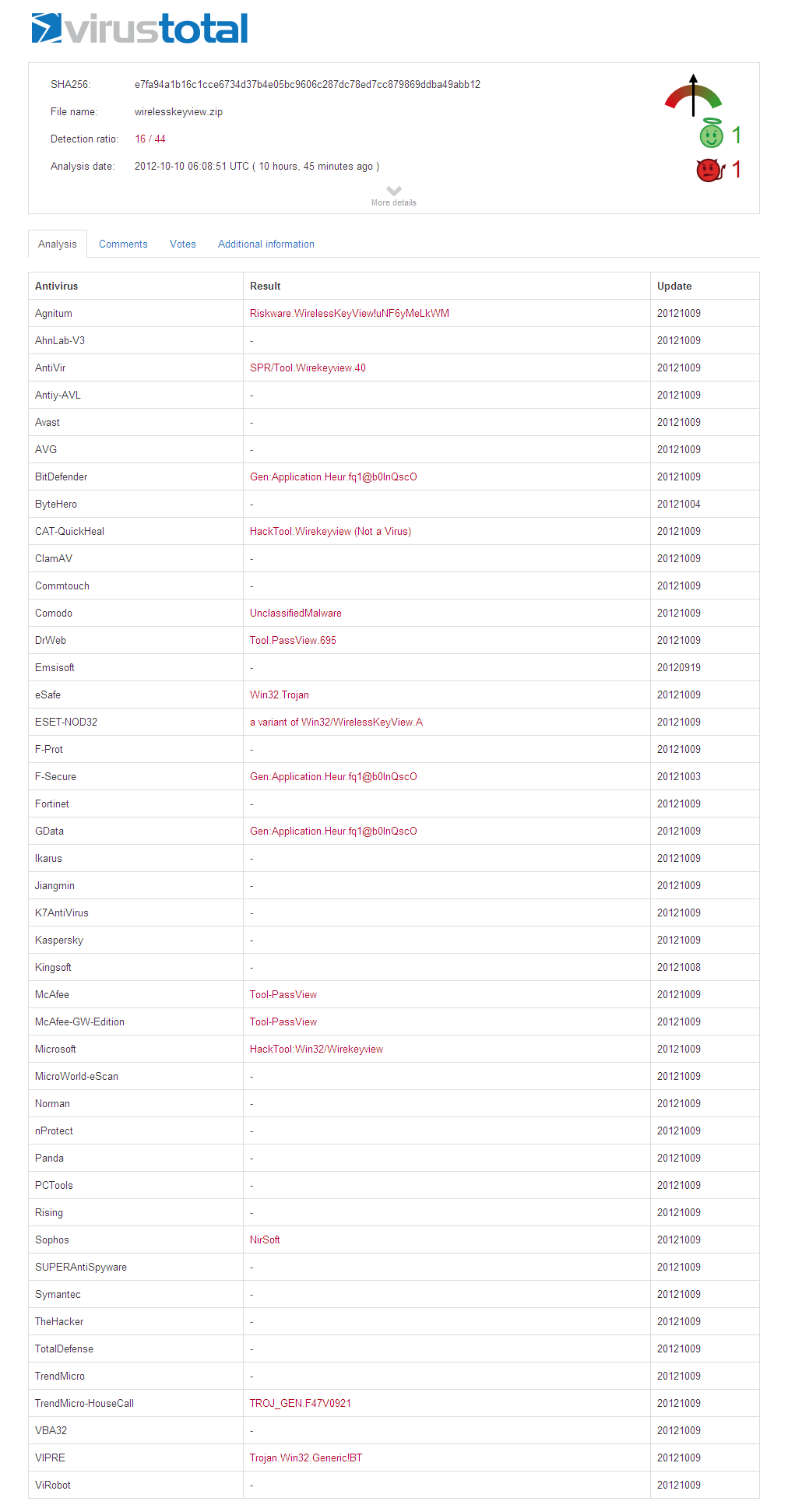
When sending the latest 32-bit version of WirelessKeyView to VirusTotal Web site, it shows false positive alerts from 16 different Antivirus programs:
Many people think that VirusTotal Web site can be used to find out whether a software is good or bad. Google probably thinks that too, because just recently they purchased this VirusTotal Web site. But the above sample proves that it’s not correct. WirelessKeyView is a completely legitimate software to get the wireless keys stored on your own system and to move your wireless keys from one compueter to another. As opposed to many other “Freeware” distributers, my software doesn’t send any personal information, doesn’t install any unwanted toolbar/spyware/malware, and doesn’t make any change in the Registry, so there is no any good reason to warn and scare the user who downloads my software.
If the 32-bit version of WirelessKeyView triggers 16 Virus alerts, you may expect that the 64-bit of WirelessKeyView , which is compiled from exactly the same code will also trigger exactly the same 16 Virus alerts.
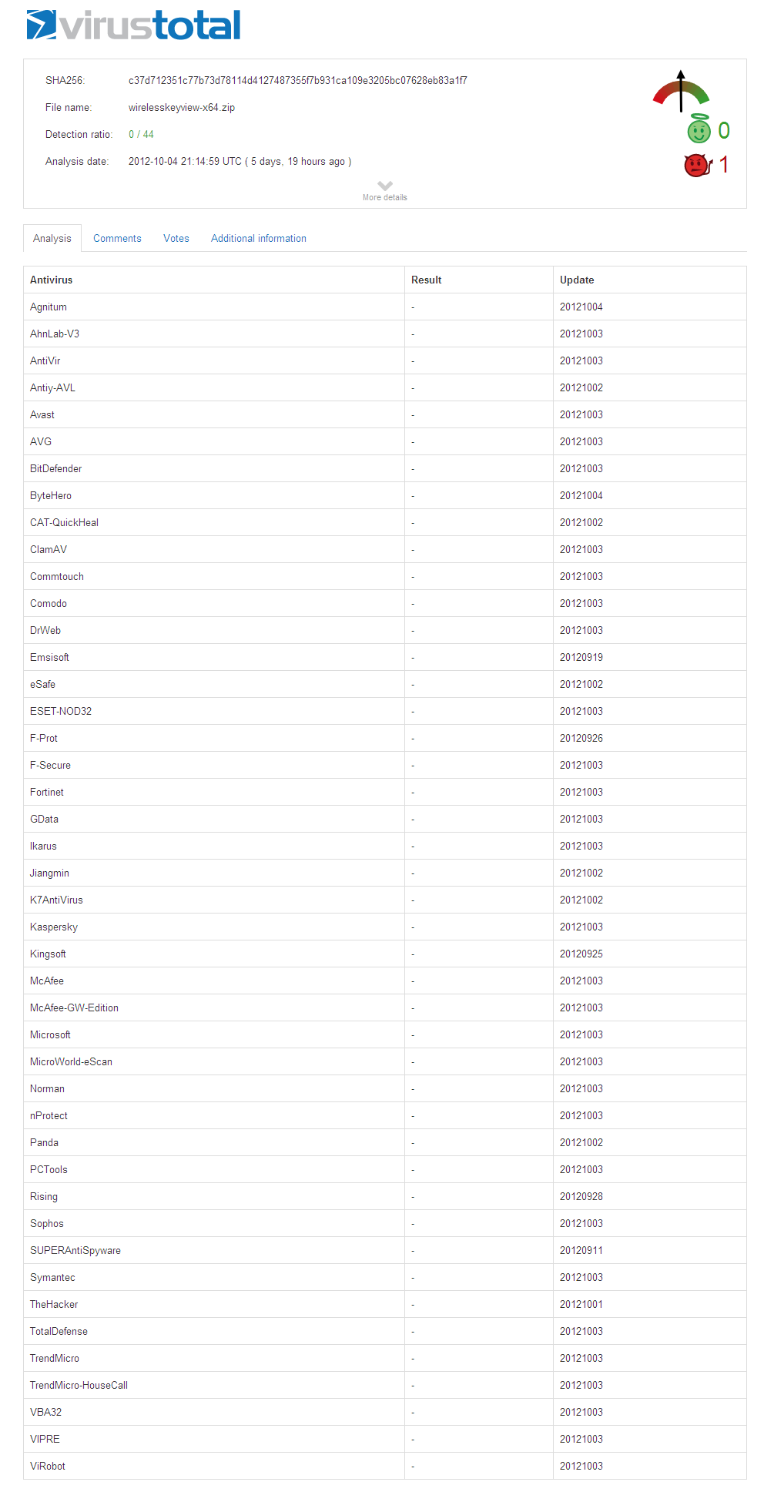
So here’s the surprise… The number of Virus alerts of WirelessKeyView 64-bit is zero !! Yes, there is no even a single Virus alert !
So what is the explanation for the difference between the alerts of 32-bit and 64-bit versions ?
Well… This question should be sent to the Antivirus companies… But I have a theory:
Looking in the downloads statistics from the last month (September 2012), the 32-bit version of WirelessKeyView (wirelesskeyview.zip) has been downloaded 313,458 times,
while the 64-bit version (wirelesskeyview-x64.zip) has been downloaded only 50,799 times.
So maybe the 32-bit version of WirelessKeyView get false alerts simply because it’s much more popular than the 64-bit version ?
When a download is more popular, there is an higher chance the somebody will use for bad purpose and the Antivirus company will get a report about that, for example: A person allows his good friend to access his computer, but his friend uses it to run WitelessKeyView 32-bit and get access to some wireless networks that it shouldn’t have access to. When this person discovers that his wireless keys have been stolen by his “friend”, he send a complaint to the Antivirus company with a sample of WitelessKeyView. In the next day, the people of the Antivirus company decide to set an alert for WitelessKeyView in order to prevent future wireless key stealing. But now many people who want to download WirelessKeyView 32-bit for good purpose, like recovering their own wireless key or moving it to another computer, get a warning from their Antivirus software or from VirusTotal Web site, without understanding the reason of getting this alert.
On the other hand… if somebody tries to use WitelessKeyView 64-bit for bad purpose, the Antivirus won’t show any alert, simply because the 64-bit version is less popular and nobody complained that it has been used to steal wireless keys.
Just a guess…
Recently I purchased a digital signature and both 32-bit and 64-bit builds of WirelessKeyView are signed with it. Some people told me that signing the .exe files will decrease the false positive alerts. So is it really help ? Maybe a little. I checked an older version of WirelessKeyView (32-bit), and VirusTotal shows 23 alerts:
https://www.virustotal.com/file/bb9bb534858fb79cb58b4a5411edd59c1b8b3390eb11635294f606f9950c595c/analysis/1349885723/
So 16 alerts is a little better than 23 alerts, but it’s still too much.
Finally, here’s 2 small articles related to false positive issues posted on other Web sites:

Shawn says:
I suspect it’s more likely the problem is related to people downloading the 32-bit version on a 64-bit computer, where it doesn’t work, so they assume it must be “bad” for you. However, since there’s no way to know why the companies flagged the software one way or the other, it’s all conjecture.
October 11, 2012, 2:02 amShawn says:
Have you considered building them the same was as Process Explorer and Autoruns? These programs run a single 32-bit exe that will drop the 64-bit version if it detects it’s in a 64-bit environment. You can get them from: http://sysinternals.com/
October 11, 2012, 2:05 amCorazon Guys says:
Amazing issues here. I am very happy to look your article. Thank you so much and I am looking ahead to contact you. Will you please drop me a e-mail?
October 11, 2012, 3:08 amSST says:
Signing the file will not help, because Antivirus companies, EXPLICITLY put the WirelessKeyView signature(s) in their database and they recognize it as exacly WirelessKeyView, not any thing else. It is not a generic detection that can go wrong, so by definition, it can not be a False Positive, but a DECISION. That made by some AntiVirus companies to warn the users, about the potential malicious usage of the utility. Though it is NOT malicious by itself. So they don’t care if it has digital signature or not.
But now you’ve purchased a digital signature, you should sign all of your utilities, not just WirelessKeyView or a few other utilities that will trigger the Antivirus alerts. This way, end users can at least be sure that, they have genuine untouched – unmodified – uninfected copies of Nirsoft utilites at hand.
October 11, 2012, 7:24 amwhocares says:
as SST said it’s sometimes a conscious decision made by the AV company to warn its users about the potential malicious use of the software and sometimes it’s just heuristics, in the you’re injecting code into another process, that’s not nice 😉 And then of course there is a third option… they don’t support 64bits application as they claim ^^
October 11, 2012, 5:28 pmAbout the signature that will help for sure.. BUT have you tried, just for fun to put a FAKE signature and see if you get the same results of a genuine one ?
Scott says:
Antivirus vendors have developed detection categories for tools that have the *potential* for malicious use in the hands of e.g. an unethical user, even while intended for legitimate and ethical uses. You can see evidence of those categories in many of the threat names listed in your virustotal report. Looks like Sophos even gave you your whole own category. This is a matter of interpretation and trusting your users to know the difference. A script kiddie that would use WirelessKeyView in an unethical way does not know the difference and neither for that matter does his victim. So it’s a grey area, and that’s what the detection is trying to express.
October 11, 2012, 7:31 pmFoolishTech says:
As SST said, it’s a decision, and it’s because of the *potential* to use your software maliciously. Also, signing does not help, that’s urban legend. I’ve been down that road. I suspect that the signing changes the file slightly enough that the sig is different and the A/V no longer recognizes it – the effect should be temporary however.
I have issues with my own software being flagged by various vendors. Though most are very receptive at fixing the issues (and in a fairly timely manner) Microsoft is the bad one. I went back and forth with their malware team for about 5 months over one of my products, which downloads / executes other apps, but ultimately they made a DECISION to blacklist my app because it downloads other software without “prior user consent” … so when I added the CONSENT prompts before download WITH cancel option and submitted back to MS for review, they said the same thing, no consent. I think they smoke crack over there – that or they just have it out for me.
Interestingly enough that app has a close brother, which also downloads / executes apps (some of them are yours, which is great software btw) and it’s exactly the same code base – yet MS doesn’t detect it yet. Its only because they haven’t noticed……
Either way, Microsoft aside because they won’t help I guarantee, but you should submit more of your apps to more vendors as false positives. Most of the time, a mere false positive submission means NOTHING because what company would take your average end user at his/her word that software is legit — however some vendors have a VENDOR submission form designed for the AUTHOR of the software to submit — not end users. This I find usually works well.
October 11, 2012, 9:11 pmchort says:
Some of you have no idea what you’re talking about. Look at the threat label–a bunch of them indicate detection by heuristics, not specific signatures. Those were obviously NOT decisions by humans.
October 11, 2012, 10:50 pmScott says:
Are you talking about the 3 heuristics detections out of 16?
October 11, 2012, 11:43 pmNirSoft says:
I know that in the most alerts it’s a matter of decision made by Antivirus companies, but I still consider it as false positive, simply because many users (especially novice users) who get an alert when downloading my software or when they see a large number of alerts in VirusTotal Web site, simply think that the file contains a Virus or it’ll do something bad to their computer. A novice user don’t understand
that a software get alerts from the Antivirus just because someone out there used it for hacking.
In my perspective, if there are people who think that I have a Virus in my software, then the alert is false. 😉
The fact the 64-bit version has zero alerts while the 32-bit has 16 alerts, just show us how much the decisions of the Antivirus companies are ridiculous
The decisions of the Antivirus companies also have many side effects, just for example:
At some point, Chrome Web browser started to block all the downloads from my Web site and say they are malicious, just because their automatic scanning systems detected many “malicious” files on my Web site.
Like a novice user, the automatic scanning system of Google (which is probably based on some popular Antivirus scanners), cannot distinguish between a real Virus/Trojan and a legitimate software that can be used for hacking.
If the Antivirus companies want to warn about a software that can be used for bad purpose, it’s completely fine, but they need to make a full separation between real Virus/Trojan designed for malicious purpose and a legitimate software that might be used for hacking.
This separation should also be applied to all scanning services provided by the Anivirus companies, like VirusTotal Web site and the Virus scanning made by Google,
October 12, 2012, 7:17 amso VirusTotal, for example, will show 2 types of alerts, one for real Virus/Trojans and other for a security risk, and
Google Chrome will block downloads only if they are detected as real Virus or Trojan.
tony meman says:
Antivirus will detect programs according to very basic signatures or hash sums of the executable. Dont expect that they can translate from 32 to 64 bit or vica versa.
October 12, 2012, 7:47 amSST says:
Yes, you are right. To the end users, specially novice ones, the result is the same: The software is bad.
Although most of the Antivirus softwares categorize them as HackTool or Tool-PassView or similar, but many of the users don’t understand the meaning of these words. It is also annoying for expert users who knows that the software is not malicious, because they have to remember to disable their security product each time they want to use such software.
But maybe you(and of course we) can get rid of or at least decrease, say, these False alerts, If you release two separate versions of these special softwares. for example safe and unsafe or whatever attribute you desire.
In the safe versions remove the ability of these softwares to be used silently and in scripts, by removing all the command line processing logic from them. And require the users provide their windows logon credentials to the program to prove that they are the real owner or user of the machine. Also, usage of the software should be restricted to the administrators. I know that some of the utilities like WirelessKeyView or DialupPassView can’t be run under the context of a limited user even if they want to, but some others like ProduKeyView doesn’t need the administrative privilages, so they should be restricted to be used only by administratos.
By doing this, the Antivirus companies may decide to not to put the safe version of the sotwares in their blacklist. I think it’s worth the try. at leat it is less expensive than a digital certificate.
October 12, 2012, 8:52 amFoolishTech says:
chort, no we have plenty of an idea of what we’re talking about when we say it’s a DECISION — you’re just not getting the complete picture here (…and I’m phrasing this a bit nicer than your put down.) A/V heuristics are only part of that picture. Yes, some detections are by heuristics, and we know how they work.
In my case, my app was undetected for some time, and a particular code change I made one day caused it to be detected by heuristics of Microsoft Security Essentials as Win32/Malintent with a HIGH risk rating, and removed it automatically.
After reporting this as a false positive, the Microsoft team actually paid attention! They examined my app, and made a DECISION, based on the criteria they list HERE: http://www.microsoft.com/security/portal/Shared/ObjectiveCriteria.aspx
As part of their DECISION they decided to label it differently, this time calling it Win32/Dsupport (after the app’s name) and no longer remove it automatically, but they still prompt the user that it is potentially unwanted software and the defaut action is removal.
They have also since added it to Windows Defender, which doesn’t remove it automatically, but doesn’t prompt you about it either, it simply (and silently without alert) prevents my app from execution.
I even have my own page at microsoft.com because of this DECISION! http://www.microsoft.com/security/portal/Threat/Encyclopedia/Entry.aspx?Name=Program%3aWin32%2fDSupport
So yes, heuristics do get the ball rolling sometimes, but it’s the DECISION by the A/V vendors to allow the heuristics to continue to detect the app (as they do with many Nirsoft apps), whitelist it from further detection, or completely blacklist it in their signature based definition files (as they did in my case).
October 12, 2012, 11:16 amMikeV says:
Welcome to the world of big business, Nir.
Please dont sign your software on my behalf. I have never needed it, and to be honest, false positives are a great way to find antimalware and antivirus software that is supported by attentive developers that actually READ submitted reports from users. ie: if you report a false positive, and your antivirus screams the next time you install that same program or upgrade it, you have a clear signal of which program needs uninstalling.
Your successful software does not need the blessing of big businesses, like the antivirus and antimalware vendors, or anyone else. Your software is far more legitimate than theirs. It has you as it’s sole cornerstone, and we fans it’s modest “sellers”.
You could quite easily campaign against all those that subvert your hard work, repaying it with lies, and it would only serve to draw more attention to these closed-loop corporations that sell more because their detectors make more noise than the other guys. This blog entry is a perfect example. Quiet, honest, and lucid. There are thousands just like you, and in time, the ignorance these companies display and/or purposely choose to adopt as a standard policy will only serve to harm them more.
eMule has been targeted by many for years, and it hasn’t harmed it it.
Carry on, Nir.
October 15, 2012, 4:13 pmYou’re more popular than they ever wish they could be.
Poli says:
My Eset Smart Security, doesnt show threat
October 23, 2012, 2:29 pmAmos says:
I had the same problem with my application. 64bit version was clean while the 32bit version was less lucky, in my case it had only 1 AV with a false positive: McAfee-GW-Edition and the detection was: Heuristic.LooksLike.Win32.Suspicious.N!83.
Few months back, there were 3 false positives so I sent each and every AV company an email with the file asking them to fix it, most of them did it after one request, for others it took some more time.
While mcafee itself is OK, GW edition of it, is generating a warning, sending an email to mcafee doesn’t help so eventually a VirusTotal guy gave me the email (that you can find nowhere!) of gw edition directly. I emailed them and they fixed it.
Several versions later, again, (only) gw edition has a false positive detection (of only the 32bit version)… now I’m looking for their email again (this is how I got to this post). It’s a never ending race…
November 7, 2012, 5:55 amAmos says:
One more thing I just remembered: I once contacted one of the AV’s (don’t remember which) in order for them to remove the false positive detection and they actually told me that the engine used by VirusTotal is used ONLY by VirusTotal, mostly as a test case, and no users of the actual product encountered this false detection.
We can try to lower the expectations from VirusTotal service but the bottom line, I think it is a very good service (and it’s free) for us, both as the users (of other applications) and as the developers (of our applications).
November 7, 2012, 7:05 am90 says:
@Nirsoft
You are right; in my opinion, the real problem here is not that your software is recognized by AV products. Malware makers push copies of your recovery programs to bots in order to steal passwords.
The real problem is that AV products fail to explain when they should trust a program. Something like “this program can be used maliciously, but if you downloaded it yourself it’s most likely fine” would suffice.
Instead, AV programs show very scary (especially to novice users) warnings that make it appear the AV just saved them from something horrible. That’s good for their sales, because it convinces users they need their product, but it’s rude to program developers and misleading to users.
June 27, 2013, 9:30 amOgier the Dane says:
It’s one thing that a software can be used malisciously if the user chooses to do so.
It’s another thing that a software is programmed to act malisciously without the user’s knowledge and consent.
A malicious user is one thing. A malicious software is another.
Antivirus companies are runned by morons who can’t tell the difference, or don’t care.
Not even when the software is digitally signed.
That’s why some of the excellent and globally recognised tools from NirSoft have problems.
Antivirus products have no business interfering with software that requires the user’s knowledge and consent to act maliciously.
I can use Microsoft Word malisciously too, if I choose to do so. For example, it’s used every day by morons at antivirus companies. Should Microsoft Word be listed as malware too?
It’s ironic that some of the tools from NirSoft are listed as malware by an antivirus product from the very same company that issued the digital certificate used to sign those tools, Comodo. Anyone can check in the file properties that this certificate was issued on September 17, 2012. That’s more than three weeks before the VirusTotal report in this blogpost was created.
Can you imagine any bigger morons than that? And they claim they offer s e c u r i t y ?
December 21, 2013, 10:11 pmKen says:
In Jan 2018, Symantec quarantined some non-password recovery Nirsoft AND *SysInternals* utilities. They were marked as trojans, not PUPs. All files were untouched for at least 6 years. Now of course anti-malware programs hate Nirsoft, but Microsoft’s own? And that got me thinking something else was the cause of heuristics going haywire.
It turns out it was UPX. Russ doesn’t compress SysInternals tools, but I did years ago.
Many 32-bit tools that have not been updated were originally compressed with UPX by Nir years ago, and I believe it is contributing very heavily to the rate of false positives reported by heuristic scans.
64-bit Nirsoft utilities are NOT UPX Compressed. This is probably why they have a much lower false positive rate.
May 18, 2018, 1:24 pmn9 says:
Note that the Microsoft AV quarantines (=deletes) your software, with no choice given to the user, because it is a “HackTool”. I bet you could sue them.
July 15, 2021, 10:35 amDiego says:
Are False-Positives worst than False-Negatives?
I think False Positive could be solved by Auditing the software itself with the developer owner and allowing to correct or explain the issue, Although I don’t think that antivirus companies actually provide a method for that.
Also “Potentialy malicious software” is not the same as “confirmed-malicious” software. But antivirus companies and malwares don’t have a correct gray-scale about it.
August 31, 2021, 1:54 pmEP says:
even the newest version of WirelessKeyView app v2.23 seems to quietly get removed by recent Windows Defender (now called Microsoft Defender Antivirus) updates in recent Windows 10/11 versions
May 21, 2024, 12:20 pm